In the JWT of Keycloak, two roles information.
It is not represented user's assigned role. Just assigned client role are included but realm's roles is possible list of realm.
If you want to get all of assigned role, have to call role mapping of user API (see #3.1)
I decoded JWT by jwo.io after get access token by Postman with Keycloak v 19.0.2
#1 realm roles list - It is not assigned realm role list, it is possible role list
User JWT(access token), get grant_type = password
{
"exp": 1669599866,
"iat": 1669596266,
"jti": "ad4e3b51-b23e-4abb-aba6-0099bb5213cf",
"iss": "http://localhost:8080/auth/realms/example",
"aud": "account",
"sub": "fae8bf9b-2209-4f01-ab32-629e029941ba",
"typ": "Bearer",
"azp": "spring-client",
"session_state": "8debdcfa-4252-4a27-8190-2a4981e6a795",
"acr": "1",
"realm_access": {
"roles": [
"offline_access",
"admin",
"default-roles-example",
"uma_authorization",
"user"
]
},
"resource_access": {
"spring-client": {
"roles": [
"client role2"
]
}
},
"scope": "openid profile email",
"sid": "8debdcfa-4252-4a27-8190-2a4981e6a795",
"email_verified": false,
"name": "first last",
"preferred_username": "user",
"given_name": "first",
"family_name": "last",
"email": "user@test.com"
}
five realm's roles are possible realm's role not assigned user's roles

User just assigned three realm's roles
Client JWT(access token), get grant_type = client_credentials
{
"exp": 1669597154,
"iat": 1669593554,
"jti": "ff6ae9db-7e05-4f9a-a538-0755a7f55125",
"iss": "http://localhost:8080/auth/realms/example",
"aud": "account",
"sub": "9db11aa2-6862-4ebb-9ee6-b03b51d7814d",
"typ": "Bearer",
"azp": "spring-client",
"acr": "1",
"realm_access": {
"roles": [
"offline_access",
"default-roles-example",
"uma_authorization"
]
},
"scope": "openid profile email",
"clientId": "spring-client",
"clientHost": "172.19.0.1",
"email_verified": false,
"preferred_username": "service-account-spring-client",
"clientAddress": "172.19.0.1"
}
Those are client's roles, it has three roles but not matched JWT's realm list
In the JWT (client access token), that list is possible realm list(not assigned client realm roles)
#2 client role - It is assigned client list
GET {KEYCLOAK-IP}/auth/admin/realms/{REALM-NAME}/clients/{client-UUID}/roles
http://localhost:8080/auth/admin/realms/example/clients/1cb76d56-b96f-42a7-91c0-c201a7761e9e/roles
[
{
"id": "e5171eb5-976e-429f-914c-0d63d7b394fd",
"name": "client role2",
"composite": false,
"clientRole": true,
"containerId": "1cb76d56-b96f-42a7-91c0-c201a7761e9e"
},
{
"id": "293c9c9c-bb76-4192-be09-ede769458394",
"name": "uma_protection",
"composite": false,
"clientRole": true,
"containerId": "1cb76d56-b96f-42a7-91c0-c201a7761e9e"
},
{
"id": "e1441ceb-7ea8-436b-9a55-30999c6de744",
"name": "client role1",
"description": "",
"composite": false,
"clientRole": true,
"containerId": "1cb76d56-b96f-42a7-91c0-c201a7761e9e"
}
]
#3 user's role list can get the separate API
3.1 all of user's role
GET {KEYCLOAK-IP}/auth/admin/realms/{REALM-NAME}/users/{USER-UUID}/role-mappings
UI:
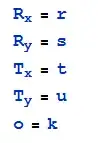
It seems to block, UI not allow to assign directly a user into client role from UI. I use REST API call. Here
Example, get user's roles:
http://localhost:8080/auth/admin/realms/example/users/fae8bf9b-2209-4f01-ab32-629e029941ba/role-mappings
Response
{
"realmMappings": [
{
"id": "c31bd5ce-e400-4546-b633-d4d5bde596d8",
"name": "admin",
"description": "Administrator privileges",
"composite": false,
"clientRole": false,
"containerId": "e78f0c77-b44b-48da-850b-9d157e24a439"
},
{
"id": "d99f61be-bacd-438d-974d-06a006704a1e",
"name": "default-roles-example",
"description": "${role_default-roles}",
"composite": true,
"clientRole": false,
"containerId": "e78f0c77-b44b-48da-850b-9d157e24a439"
},
{
"id": "8d250d6c-e249-4b63-b86f-390b4550b12e",
"name": "user",
"description": "User privileges",
"composite": false,
"clientRole": false,
"containerId": "e78f0c77-b44b-48da-850b-9d157e24a439"
}
],
"clientMappings": {
"spring-client": {
"id": "1cb76d56-b96f-42a7-91c0-c201a7761e9e",
"client": "spring-client",
"mappings": [
{
"id": "e5171eb5-976e-429f-914c-0d63d7b394fd",
"name": "client role2",
"composite": false,
"clientRole": true,
"containerId": "1cb76d56-b96f-42a7-91c0-c201a7761e9e"
}
]
}
}
}
If you want to see, how to set the role into client or user,here